You cannot trace text messages back to a sender as an end user. Carriers can follow an SMS through their Short Message Service Centers and law enforcement can request those records with a warrant. You do not have access to those systems. Your best moves are simple. Save evidence. Block the sender. Report smishing. Verify any claim through official apps or websites.
Why tracing a text is hard for regular users
Tracing a text looks simple from the outside. Behind the scenes, messages pass through carrier equipment you cannot see. The proof you want lives in closed systems that protect customer privacy and network reliability.
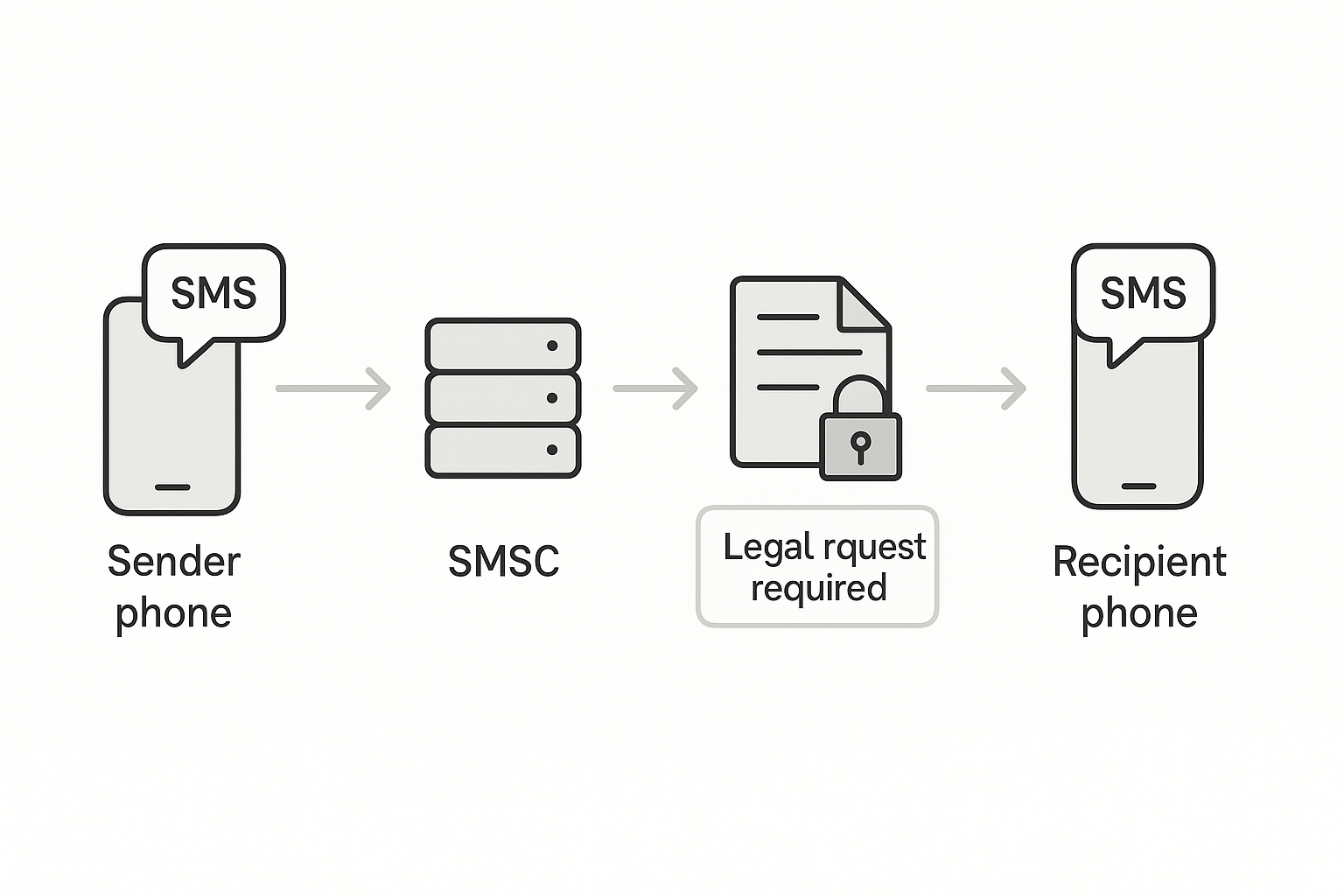
The path an SMS takes across carrier networks
Text messages travel from a sender phone to a cell tower, then into an SMSC. The SMSC stores and forwards the message until your device connects. Carriers log these hops for uptime, billing, and lawful requests. Those logs are not public.
The data you cannot access as a consumer
Carriers keep delivery time stamps, routing decisions, and limited metadata. They do not expose subscriber identity or routing history to the public. Any app that claims to show this for a stranger’s message is not telling the full truth.
The risk of overreaching with third-party tools
Apps that promise full tracing often request invasive permissions or money before results. Many recycle public data or breach dumps. Some are outright scams. Even if a tool feels legitimate, using it on a phone you do not own can break laws.
How tracing happens in legitimate investigations
You deserve a clear picture of what carriers and police can do. This helps set expectations and guides your next steps if a message crosses a legal line.
What carriers actually record
Carriers retain routing metadata and SMSC handoffs. They can see which network accepted a message and where it went next. That view sits behind strict access controls. It is designed for reliability and compliance, not consumer lookups.
What law enforcement requests with legal authority
Investigators can obtain a warrant or subpoena for records. Carriers then share approved data that links message events to a subscriber account. When allowed, they can also correlate location from tower connections that place a device near a cell site at a specific time.
Limits and gray areas even for professionals
Retention windows vary by region and carrier. Number porting and cross-network routing introduce complexity. Content may not be available unless a platform stored it by design. This is why you should preserve your own evidence right away.
What you can do today without crossing legal or ethical lines
You might not trace a sender, but you can protect yourself and give authorities what they need if the case escalates.
Preserve evidence before anything changes
Take screenshots that show the number and the time. Save attachments without opening them. Write a short note about how you received the text. If the message relates to a bank or a purchase, collect proof from the official app or website.
Block and report smishing the right way
Use your phone’s spam tools to block the number. Report the message through your carrier’s spam channel. Review guidance from the United States Postal Inspection Service on package tracking text scams. They explain how to spot fakes and where to report them.
Verify claims safely without clicking risky links
Open the company’s official app. Type the website address yourself in the browser. If the text mentions a delivery, enter the tracking number on the carrier’s real site. Never sign in from a link you did not request.
Use your own accounts and devices correctly
Some carriers and platforms let you check text messages online for your own number. Use this only behind strong authentication. In business tools, you can view text messages sent and received by numbers your company owns. Lock that access to admins and audit it.
Reading signals in links, images, and message content
You cannot unmask a sender with certainty, but you can read signals that help you decide what to do next.
Links that try to rush you
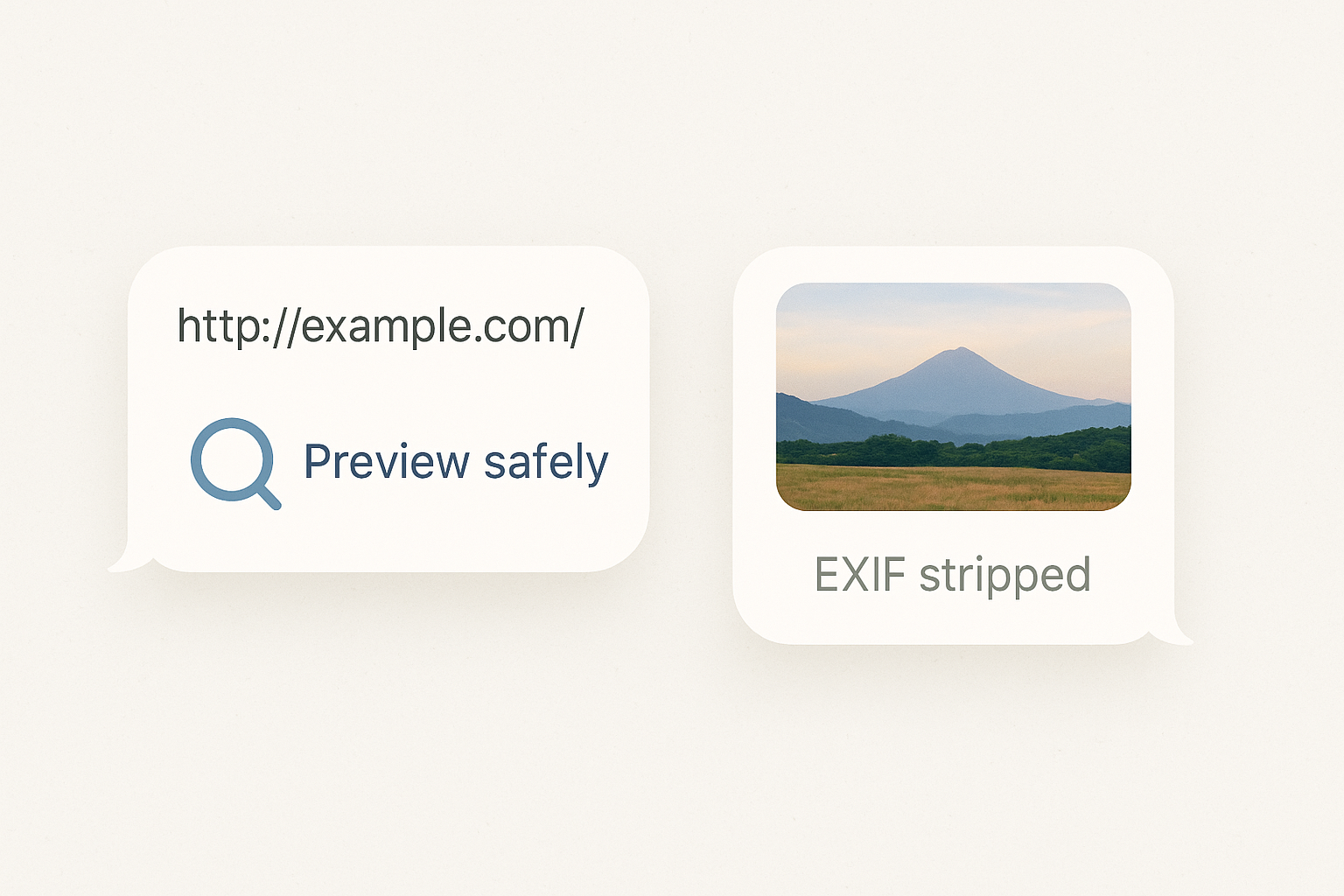
Shortened links hide their destination. Use a preview tool that shows the target without loading scripts. Watch for lookalike domains and misspellings. If a link claims to be from a brand you know, compare it to the brand’s real domain. If anything feels off, close the tab.
Attachments and photos that carry clues
Messaging apps often strip location data from images. A photo might still contain EXIF hints if the sender used an app that kept them. Treat EXIF as a clue, not proof. Never open files that ask you to enable macros or install additional software.
Content that hints at a location or identity
A mention of a city, a storefront, or a niche product can reveal a target audience or marketing list. Use these hints to guide your response. They do not replace verification through official channels.
Common myths, traps, and dead ends to avoid
You will see search terms that promise more than they deliver. Use them carefully to avoid scams and wasted time.
The lure of a “message tracker” that unmasks strangers
A site that claims to trace any number does not have access to carrier routing data. At best it guesses from public records. Treat these services as red flags.
Can text messages be traced back by carriers
Yes, carriers can correlate logs to a subscriber with legal process. That power does not extend to the public. Any tool that says otherwise is misleading you.
No such thing as an official “google sms tracker”
Google does not offer a tool that reveals who sent a random SMS. Family-safety products work only on devices you own and manage with consent.
Ignore pitches that mention an “sms tracking number”
Carriers use internal identifiers to move messages. They do not publish a tracking number you can paste into a website. Anyone who sells that idea is selling fiction.
Be careful with “sms tracker android” or any “sms tracker app for android”
Only install device-management tools on phones you own and manage with the user’s consent. Using them on someone else’s device can break laws and trust.

For businesses that send or receive a lot of texts
Companies face bigger stakes. A single smishing wave can spike call volume, damage trust, and pull agents away from revenue work. Build guardrails now.
Consent and compliance that stand up to scrutiny
Capture explicit opt-in at sign-up. Store the time and the method. Honor opt-out immediately. Train staff on approved use cases and tone. Keep templates for sensitive messages like payments and deliveries. Review them quarterly.
Audit trails that show what you sent and why
Centralize outbound and inbound logs in your messaging platform. Tag by campaign and sender ID. Keep the ability to export logs if a carrier or regulator asks for them. Use analytics to watch delivery rates and reply spikes.
Clear public guidance for customers
Publish a page that explains how you text customers. List your short codes and sender IDs. Teach people how to verify a real message and how to report a fake. Share this page in onboarding emails and on your help center.
Operational response during a smishing wave
Assign one point of contact in security and another in customer care. Give agents a short script that explains next steps and points to the verification page. Escalate examples to your carrier’s enterprise abuse channel. If threats or fraud appear, file a police report and include your logs.
Where SuperU helps when texts turn into calls
Texts that confuse people turn into calls. SuperU answers around the clock, screens spam calls that follow smishing, confirms official information, and routes real customers to the right person. You keep agents focused while protecting reputation and trust.
Practical tools that strengthen your position
You do not need tracing powers to reduce risk today. These steps raise your floor on both personal and business phones.
Strong authentication and recovery hygiene
Use a password manager for unique passwords. Turn on two factor authentication for email, banking, and cloud accounts. Remove recovery methods you no longer use. Audit which apps can read SMS for codes.
Device settings that reduce exposure
Keep your operating system and apps updated. Limit notification previews on the lock screen. Review app permissions and remove ones you do not recognize. Back up your phone so you can reset it if needed.
Carrier features worth enabling
Ask your carrier about network-level spam filtering. Learn the exact path to report spam from your phone. If your number gets ported without consent, know who to call and how to restore service fast.
FAQs
1. Can my carrier tell me who sent a harassing text?
Carriers generally share identity and routing data only with law enforcement after a legal request. Ask police to file a report if you face threats or stalking.
2. Does deleting a thread destroy evidence?
No. Carriers keep logs for a period. Still, keep your own screenshots and notes. They help support your case.
3. Does a VPN hide my texts ?
No. SMS travels on the cellular network rather than your internet connection. A VPN changes your internet path, not your SMS path.
4. Can I trace texts from web-based messengers ?
Platforms keep server logs that can be requested by law enforcement. You cannot unmask a random user from the outside.
5. Do photos in texts reveal where they were taken?
Most apps remove location data to protect privacy. If you see any EXIF details, treat them as hints and verify through other sources.
6. How do I verify a delivery text without risk?
Open the shipper’s app or type the official website into your browser. Enter the tracking code there. Do not click links from texts you did not request.
Conclusion
You cannot trace a text like a carrier can. Focus on actions that protect you. Save evidence, block and report smishing, and verify through official apps or sites. If threats or fraud appear, involve police and your carrier. Businesses should harden consent, logs, and public guidance to guard customer trust.
Book a five-minute SuperU demo to calm smishing-driven call spikes.
Start for Free – Create Your First Voice Agent in Minutes


